Level 3 Advanced Mobile App Security
- Helps your apps become self-defending against malware attacks.
- Integrates seamlessly into your Enterprise app store with our Level 3 Subscription Option.
- Provides unified licensing and support. Requires no separate licenses or contracts with third party vendors.
- Advanced mobile app security can be applied to selected apps that need advanced protection.
- Security features are applied without an MDM profile, assuring that your employees data remains their data.
When You Release An App To Your App Store…
You Must Protect It From Ferocious Security Assaults
App47™ provides security elements for individual applications.
It protects not only the application itself—when downloaded to a device. It also protects the platform elements which the app relies on to execute.
- App47 provides Self-Protection abilities to both Mobile apps and Desktop applications. It supports iOS and Android. Easily turns your apps into self-protecting apps.
- App47 monitors and controls the execution of the application. This includes interactions with OS components, protecting the app from attacks and data exfiltration.
- It provides Obfuscation, Anti-tampering and Integrity Checking, as well as White-box Cryptography and many other security features.
- Once secured with App47, your app is immediately ready for distribution from your enterprise app stores.


Some Of The Risks Of Releasing An App In Your App Store
Unfortunately, releasing an app in your app store means you have to protect against malicious intentions. Some malicious activities are done just to prove a point. Others aim to do serious harm to your app, data, or enterprise.
It’s easy enough for attackers to reverse engineer virtually any app they download from your app store. They can wreak havoc with the way your application runs individually or enterprise wide. You could have stolen credentials that then then trick users into downloading and installing a modified version of your app.
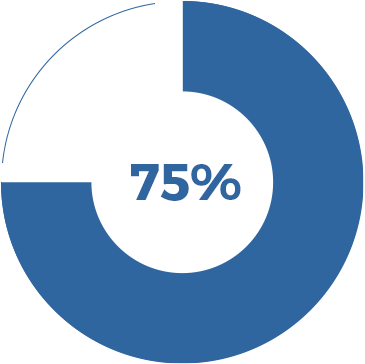
GARTNER says, “75% of mobile applications would fail basic security tests.”
If you have security responsibility for the in-house app store, that’s a nightmare statistic.
App47 Mobile App Security Protects Against these Threats:
- Rooting and jail-breaking information
- Repackaging detection/prevention information
- Hooking framework detection/prevention information
- Untrusted Screen-reader detection/prevention information
- Untrusted Keyboard detection information
- Screen-shot/screen-capture detection/prevention information
- PIN Code enablement/management
- External Screen detection/prevention information
- Runtime integrity check information
- Debugger detection/prevention information
- Emulator detection/prevention information
- Native Code Hook detection/prevention information
- Runtime Library Injection detection/prevention information
App-Centric Security Supplemented by Device Level Protection Features
Rather than rely on the “sledgehammer” approach of device-focused control, we secure data at the application layer—enabling BYOD environments without sacrificing security. Key device-level security features—like wiping an app’s private data—are still available when devices leave your control. This best-of-both-worlds approach maintains flexibility while letting you protect data both on-device and in-transit while enabling mobile productivity for your workforce. To learn more about how, with the right tools, a MAM strategy can protect your from 99% of vulnerabilities (even without any MDM profiles) check out our recorded webinar here.
We’ve thought carefully about how to mitigate a huge array of vulnerabilities using our MAM foundation:
- You can configure App47 to automatically check for access rights at an interval of your choosing—if a user no longer has access, they can be locked out of your enterprise apps and lose access to the sensitive data within.
- Geo-Fencing allows you to restrict access to enterprise apps by location. This control can range from high-level backstops (like preventing sensitive data from being accessed outside the country) to highly-specific operational restrictions using specific coordinates (like preventing embedded devices from accessing your apps if taken off-premise).
Our “time-bomb” feature gives you advanced control over when applications can be accessed, and which security policies apply. From relegating app-usage to business hours, to restricting embedded device access to times relevant for actual workflows, App47 makes it easy to automatically close potential access points when they’re not actually needed by your business. An app can even be set to automatically lock or wipe if hasn’t checked in with App47 by a pre-determined checkpoint.

Managed Versioning Brings Up-to-Date Security to the App Store
Unlike consumer apps, enterprise apps can’t afford to wait for users to update at their leisure—lapsed versioning creates an acute security risk. Forced updates ensure that careless users don’t introduce costly vulnerabilities.
Keeping users using the latest update also dramatically reduces the support issues that stem from users using many different versions of the same app across the company.
Users can even ignore updates a pre-set number of times to ensure that crucial work isn’t interrupted by a poorly timed update.
Continued Updates to Respond to Emerging Threats
The mobile-security landscape is always evolving, an no static security solution can succeed. That’s why we’re constantly monitoring emerging threats, and App47 customers can rest assured that best practices will quickly be applied for mitigating or eliminating innovative new threat vectors.

Ensure Regulatory Readiness
GDPR is just the beginning. More and more governing institutions, from national to local, are adapting more and more strident data protection regimes that will only spread to include more verticals and data types. Meanwhile, B2B customers are increasingly likely to apply secure data auditing practices to major private sector partners even where not regulatorily bound.
The diversity and innovativeness of threat vectors will only continue to multiply, and this newly robust framework for protecting sensitive data is here to stay. App47 provides everything you need to prepare your EMM strategy for this next generation regulatory environment.
Download the Advanced App Security Fact Sheet
Request a Demo of App47
